Security 360o Perspective: Exposures Matter More than mere Threats.
Security 360o Perspective: Exposures Matter More than mere Threats
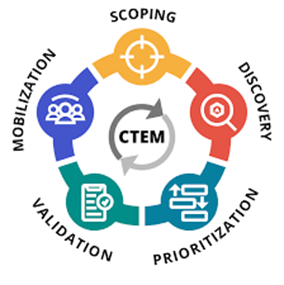
Exposure to validated threats present undeniable risk to the enterprise. Such actionable information improves Cyber Threat intelligence (CTI), enables holistic Vulnerability Management (VM), minimizes impact, and maximizes the performance of Offensive Threat (OT) activities. Clients should consider adaption of emerging Exposure Management (EM) technologies to migrate to a high-performance Continuous Threat Exposure Management (CTEM) program.
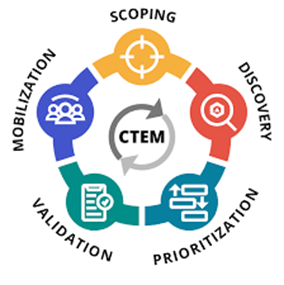
Cyber risk has always been viewed as just the threat and vulnerability to an organization’s assets. Managing vulnerability and being aware of the threats is good enough – right? Unfortunately, not. There are too many siloed vulnerability assessment services and divergent threat intelligence sources. Over a year ago, Gartner raised the issue and loudly predicted a shift from mere Threat Management to Exposure Management.[i] The new focus now shifts to Continuous Threat Exposure Management (CTEM)!
For years, the goal has been to act upon Cyber Threat Intelligence.[ii] Tools did evolve to serve the Operational and Technical stakeholders of CTI. Unfortunately, little actionable information has been available to Strategic and Tactical stakeholders. According to Gartner, CTEM sits at the intersection of Threat Detection and Incident Response (TDIR) and Governance, Risk, and Compliance (GRC) – exactly where Strategic and Tactical stakeholders operate.
In our last article[iii], we learnt that an IT Security Plan should consider Emerging technologies. Luckily Continuous Threat Exposure Management programs are evolving, and Exposure Management (EM) tools have emerged. EM is one of only two tool categories viewed as TRANSFORMATIONAL to Security Operations! [iv] EM is also to be in the MAINSTREAM in 5-10 years. Early adopters may gain significant benefit depending on where they are in terms of vulnerability and threat management. Consider EM technologies if your organization wants additional validation of its security posture, is looking for more automation in running attack scenarios, and/or wants to establish a red team with limited training or experience.
Cyber Buyer has recently partnered with Hive Pro, a Continuous Threat Exposure Management solution. Read their article to learn more about CTEM and advise if you want an introductory meeting on their solution.
---------------------------------
Donald Borsay is an advisor, auditor, and instructor, with over 20 years dedicated to Cybersecurity. Borsay is a thought leader and Security Advisor for Tech City Advisors, supporting Cybersecurity technical architecture planning and solution implementation. Feedback is welcome at: Donald.borsay@cyberbuyer.io.
Coyote Brown offers Cybersecurity Advisory, Consulting, and Assessment Services, composed of highly experienced strategic cybersecurity advisors and consultants helping clients maintain a healthy cyber security posture.
Tech City Advisors is an IT Service Provider with specialized knowledge of information technology. They have commercial partnerships with over 300 technology vendors, enabling the resale and support to clients on behalf of our vendor partners.
------------------------------------------------------
[i] Gartner - Predicts 2023: Enterprises Must Expand From Threat to Exposure Management - https://www.gartner.com/en/documents/4021605
[ii] SOCRadar - What is Tactical Cyber Threat Intelligence and How to Use it - https://socradar.io/what-is-tactical-cyber-threat-intelligence-and-how-to-use-it/
[iii] Coyote Brown - Security 360° Perspective: Commonsense Planning of Security Technologies - https://www.cyberbuyer.com/media/security-360-perspective-commonsense-planning-of-security-technologies
(G) Gartner - Hype Cycle for Security Operations, 2023 - https://www.gartner.com/en/documents/4547399
« Back to News & Media


